China's rapid expansion of distributed energy resources (DER) at low voltage (LV) levels has created unprecedented cybersecurity challenges. The DL/T 634.5.104 standard, adapted from IEC 60870-5-104, serves as the backbone for secure communication between DER systems and grid operators. With over 260 GW of distributed solar capacity installed nationwide, understanding this protocol becomes critical for anyone managing remote energy systems in China's evolving grid landscape.

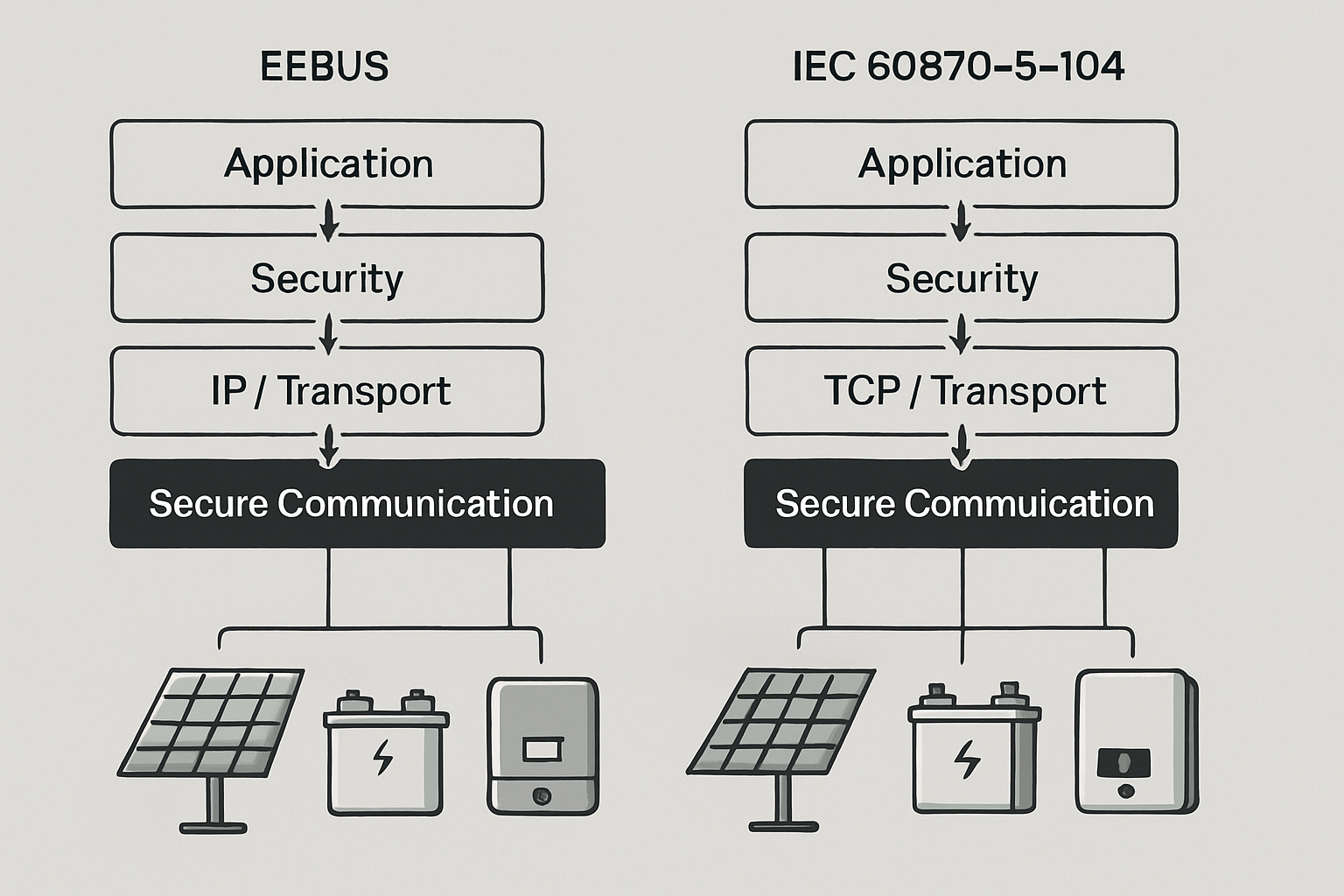
Understanding DL/T 634.5.104 Protocol Architecture
The DL/T 634.5.104 standard establishes the communication framework for DER systems operating at low voltage levels. Unlike its medium voltage counterpart DL/T 634.5.101, this protocol specifically addresses the unique challenges of LV-connected distributed resources.
Core Protocol Features
DL/T 634.5.104 incorporates several key elements that distinguish it from generic communication protocols:
- TCP/IP-based communication: Enables reliable data transmission over public networks
- Standardized data objects: Ensures consistent information exchange between different manufacturers
- Time synchronization: Critical for coordinated control actions across distributed systems
- Authentication mechanisms: Prevents unauthorized access to control functions
According to IRENA's Grid Codes for Renewable Powered Systems, "DER and microgrids connected at the low voltage level can communicate using a wireless or optical fibre public network, but information security protection measures must be in place."
Communication Infrastructure Requirements
The standard mandates specific infrastructure elements for secure DER communication:
| Component | Requirement | Security Level |
|---|---|---|
| Network Connection | Wireless or Optical Fiber | Encrypted transmission |
| Data Authentication | Digital certificates | PKI-based verification |
| Access Control | Role-based permissions | Multi-factor authentication |
| Data Integrity | Checksums and hashing | Real-time validation |
Cybersecurity Implementation for LV DER Systems
Implementing robust cybersecurity measures under DL/T 634.5.104 requires a multi-layered approach. The standard recognizes that Internet-based communication is becoming more relevant for power system operation, making cybersecurity "one of the most critical factors for the security of electricity supply."
Authentication and Access Control
The protocol establishes strict authentication requirements for all communication endpoints. Each DER system must maintain digital certificates issued by authorized certification authorities. These certificates enable mutual authentication between the DER unit and the control center, preventing man-in-the-middle attacks.
Access control mechanisms operate on multiple levels:
- Device-level authentication: Hardware-based security modules verify device identity
- User authentication: Operators must authenticate using multi-factor methods
- Function-level authorization: Different control functions require specific permission levels
- Time-based access: Critical operations may be restricted to specific time windows
Data Encryption and Transmission Security
All communication under DL/T 634.5.104 must employ end-to-end encryption using approved cryptographic algorithms. The standard specifies minimum encryption key lengths and mandates regular key rotation to maintain security effectiveness.
Data transmission security includes:
- TLS 1.3 or higher for transport layer security
- AES-256 encryption for data protection
- SHA-256 hashing for data integrity verification
- Perfect forward secrecy to protect past communications
Remote Monitoring and Control Capabilities
DL/T 634.5.104 enables comprehensive remote monitoring and control of distributed energy resources while maintaining security integrity. The protocol supports real-time data acquisition, historical data retrieval, and remote control commands.
Monitoring Functions
The standard defines specific data objects for monitoring DER performance:
- Power measurements: Real-time active and reactive power output
- Voltage and frequency: Grid connection point measurements
- Equipment status: Operational state of inverters, batteries, and protection systems
- Alarms and events: Fault conditions and operational notifications
Control Command Structure
Remote control capabilities under DL/T 634.5.104 include power curtailment, voltage regulation, and emergency shutdown functions. Each control command requires authentication and authorization before execution, with confirmation messages ensuring successful implementation.
The IEA's China Power System Transformation report highlights the importance of coordinated control for managing high penetration of variable renewable energy sources in China's power system.
Compliance Requirements and Implementation Challenges
Achieving compliance with DL/T 634.5.104 presents several technical and operational challenges for DER operators and equipment manufacturers.
Technical Compliance Standards
The standard requires adherence to specific technical parameters:
| Parameter | Requirement | Tolerance |
|---|---|---|
| Response Time | ≤ 2 seconds | ±0.1 seconds |
| Data Update Rate | 1-60 seconds | Configurable |
| Communication Availability | ≥ 99.5% | Monthly average |
| Security Key Rotation | ≤ 24 hours | Automated process |
Integration with Existing Systems
Many existing DER installations require retrofitting to meet DL/T 634.5.104 requirements. This process involves upgrading communication hardware, implementing security protocols, and training operational personnel.
Common integration challenges include:
- Legacy equipment compatibility issues
- Network infrastructure limitations in rural areas
- Cybersecurity skill gaps among operators
- Cost implications of security upgrades
Future Developments and Industry Impact
The evolution of DL/T 634.5.104 reflects China's commitment to secure and reliable distributed energy integration. As the country continues expanding its renewable energy capacity, this standard will play an increasingly important role in maintaining grid stability and security.
Emerging Technologies Integration
Future revisions of the standard are expected to address emerging technologies such as:
- Artificial intelligence-based threat detection
- Blockchain-enabled device authentication
- Quantum-resistant cryptographic algorithms
- Edge computing for reduced latency
The IRENA report emphasizes that "cybersecurity has already become one of the most critical factors for the security of electricity supply today and will become even more important in the future."
Market Implications
Compliance with DL/T 634.5.104 is becoming a prerequisite for DER deployment in China's market. Equipment manufacturers must invest in security features and certification processes, while system operators need to develop cybersecurity expertise and incident response capabilities.
The standard's influence extends beyond China, as international manufacturers seeking to enter the Chinese market must ensure their products meet these requirements. This creates opportunities for cybersecurity solution providers and drives innovation in secure communication technologies.
Key Takeaways for Secure DER Implementation
Successfully implementing DL/T 634.5.104 requires a comprehensive approach to cybersecurity that balances operational requirements with security imperatives. The standard provides a robust framework for secure DER communication, but its effectiveness depends on proper implementation and ongoing maintenance.
Critical success factors include investing in proper cybersecurity infrastructure, training operational staff on security protocols, establishing incident response procedures, and maintaining regular security assessments. As China's distributed energy landscape continues evolving, adherence to this standard will remain essential for maintaining secure and reliable grid operations.
The integration of cybersecurity measures into DER systems represents a fundamental shift in how we approach distributed energy management. DL/T 634.5.104 provides the foundation for this transformation, ensuring that China's renewable energy future remains both innovative and secure.




Leave a comment
All comments are moderated before being published.
This site is protected by hCaptcha and the hCaptcha Privacy Policy and Terms of Service apply.