Modbus and SunSpec are foundational protocols that enable seamless communication between inverters, energy storage systems (ESS), and monitoring platforms. Their simplicity and widespread adoption have made them industry workhorses. Yet, this simplicity hides a critical vulnerability that is frequently overlooked: the use of default passwords. Leaving these factory-set credentials unchanged is like leaving the front door of your power system wide open for intruders. This guide outlines the risks and provides actionable steps for cybersecurity hardening in your ESS networks.
The Hidden Danger of Default Settings in ESS Communication
Understanding the protocols is the first step to securing them. They are effective for operational data exchange but were not originally designed with modern cybersecurity threats in mind. This legacy creates inherent risks that demand proactive attention.
What Are Modbus and SunSpec?
Modbus is a serial communication protocol developed in 1979 for industrial automation. It allows devices to exchange data in a simple master-slave or client-server format. Because of its reliability and ease of implementation, it became a de facto standard in many industries, including solar energy. The SunSpec Alliance built upon this foundation, creating standardized data models that run over Modbus. This ensures that inverters, meters, and batteries from different manufacturers can communicate using a common language, simplifying system integration and monitoring.
Why Default Passwords Are a Critical Vulnerability
The primary security flaw is not with the protocols themselves, but with how they are deployed. Manufacturers ship devices with identical, publicly documented default passwords. Attackers know this and use automated scripts to scan the internet for vulnerable devices. A successful breach can have severe consequences:
- Data Theft: Attackers can steal sensitive operational data, revealing energy production and consumption patterns.
- System Manipulation: A malicious actor could alter inverter settings, shutting down power generation, manipulating grid-interactive functions, or even causing physical damage to equipment by pushing it beyond its operational limits.
- Ransomware Attacks: An entire fleet of inverters could be locked by an attacker, who then demands a ransom to restore functionality.
The threat is not theoretical. Vulnerable industrial control systems are compromised daily, and as ESS networks become more common, they become more attractive targets.
A Layered Approach to Hardening Your Network
Effective cybersecurity hardening is not about a single solution. It requires a defense-in-depth strategy, where multiple layers of security work together to protect your assets. Simply changing a password is a start, but it is not enough on its own.
Beyond the Password: Foundational Security Measures
Before focusing on the protocols, secure the environment they operate in. Foundational security practices create a strong perimeter defense.
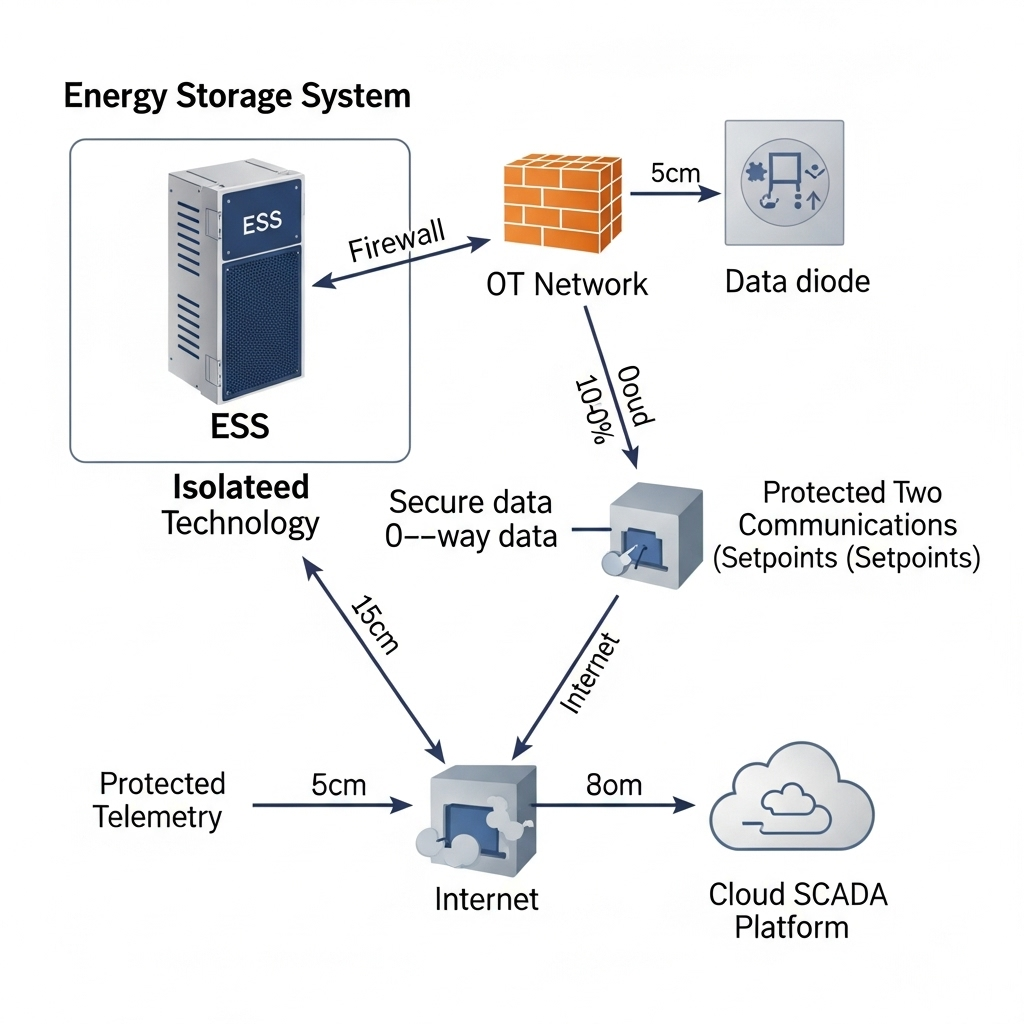
- Network Segmentation: Isolate your operational technology (OT) network, which contains your inverters and ESS, from your information technology (IT) network (e.g., corporate email and office computers). Use firewalls to strictly control traffic between these segments, only allowing necessary communication through specific ports.
- Disable Unused Ports and Services: Every open port and running service is a potential entry point for an attacker. Review your device configurations and disable any features or services that are not essential for operation.
- Physical Security: Digital security is useless if an attacker can gain physical access to your equipment. As noted in a report from the International Renewable Energy Agency (IRENA), adequate physical security is a key functionality to protect hardware from unauthorized access and malicious actions. Ensure inverters, communication gateways, and control panels are in locked rooms or enclosures.
Implementing Strong Authentication and Access Control
With the network secured, focus on who can access it. Strong authentication ensures that only authorized users and systems can issue commands.
- Change Default Passwords Immediately: This is the most critical and simplest step. Replace all factory-default credentials with unique, complex passwords during system commissioning.
- Enforce Strong Password Policies: A strong password should be long (at least 12-16 characters) and include a mix of uppercase letters, lowercase letters, numbers, and symbols. Implement a policy for periodic password rotation.
- Use Role-Based Access Control (RBAC): Grant permissions based on the principle of least privilege. An operator who only needs to monitor system performance should not have the administrative rights to change critical settings.
Advanced Hardening Techniques for Modbus/SunSpec
For high-value or critical infrastructure assets, basic measures should be supplemented with advanced security techniques that address the inherent weaknesses of Modbus.
Securing Data in Transit
Standard Modbus sends data in cleartext, meaning anyone who can intercept the traffic can read it. Encrypting this data is crucial for preventing eavesdropping and man-in-the-middle attacks.
- Modbus TCP with TLS: The official Modbus TCP Security Protocol specification incorporates Transport Layer Security (TLS) to provide authentication, integrity, and confidentiality. When selecting new equipment, prioritize devices that support this modern standard.
- Virtual Private Networks (VPNs): For legacy systems that do not support TLS, a VPN is an excellent solution. A VPN creates an encrypted tunnel between two endpoints (e.g., between a remote monitoring station and the on-site gateway). All Modbus traffic passing through this tunnel is protected from interception.
Monitoring and Incident Response
You cannot defend against threats you cannot see. Continuous monitoring and a clear response plan are vital for resilience. The International Energy Agency (IEA) emphasizes that robust monitoring is fundamental to maintaining system stability, a principle that directly applies to cybersecurity.
- Network Logging and Anomaly Detection: Log all access attempts, configuration changes, and control commands. Use monitoring tools to analyze traffic for unusual patterns, such as login attempts from unknown IP addresses or commands sent outside of normal operating hours. A sudden change in system output, for example, could indicate tampering. Understanding what normal looks like is key, and you can review a detailed breakdown of key metrics in this guide on solar storage performance.
- Firmware Management: Keep device firmware up to date. Manufacturers release patches to fix security vulnerabilities. However, ensure your firmware update process is secure. Only download updates from official sources and, if possible, use devices that support digitally signed firmware to verify its authenticity.
Comparing Security Measures: A Practical Overview
Choosing the right security measures involves balancing cost, complexity, and the level of protection required. Not every system needs a fortress, but every system needs a lock on the door.
| Security Measure | Complexity | Estimated Cost | Security Impact |
|---|---|---|---|
| Change Default Passwords | Low | Low (Time) | High |
| Network Segmentation | Medium | Moderate (Firewall hardware) | High |
| Physical Security | Low-Medium | Low-Moderate (Locks, enclosures) | High |
| VPN Implementation | Medium | Moderate (Software/Hardware) | Very High |
| Modbus TCP with TLS | Medium-High | Varies (Requires supported hardware) | Very High |
| Active Monitoring & Logging | High | Moderate-High (Software/Services) | Critical for Detection |
The U.S. Department of Energy has consistently supported the development of secure network architectures for distributed energy resources (DERs), advocating for a multi-layered approach. For a small residential ESS, changing passwords and securing your Wi-Fi network may suffice. For a commercial or utility-scale installation, a comprehensive strategy combining all these measures is essential for protecting your investment and ensuring grid stability.
Moving Beyond Default Settings for a Resilient Future
Modbus and SunSpec remain vital for the solar and storage industry, but their security cannot be taken for granted. The convenience of default settings comes at the high price of extreme vulnerability. Hardening these communication channels is not an optional extra; it is a fundamental requirement for building a secure and resilient energy future.
The journey starts with a single, decisive action: changing every default password. From there, building a layered defense with network segmentation, encryption, and active monitoring will transform your ESS network from a soft target into a hardened asset. True energy independence is built on a foundation of both reliable power and robust cybersecurity.
Disclaimer: This article provides general information and best practices. It does not constitute professional cybersecurity or investment advice. Always consult with a qualified cybersecurity professional to assess and secure your specific systems.
Frequently Asked Questions
What is Modbus and why is it a security risk?
Modbus is a communication protocol used in industrial systems, including solar inverters and ESS. It is a security risk primarily because it was designed without security features like encryption or strong authentication. When deployed with default passwords and on open networks, it allows unauthorized users to potentially monitor and control energy systems.
I changed the password. Is my system completely secure now?
Changing the password is the most important first step, but it does not make a system completely secure. A layered security approach is necessary. This includes securing the network with firewalls, encrypting traffic with a VPN if possible, disabling unused services, and regularly monitoring for suspicious activity.
Can I add encryption to my existing Modbus system?
Yes. Even if your devices do not natively support encrypted Modbus, you can secure the communication channel. The most common method is to configure a Virtual Private Network (VPN) between your devices and the control center. This creates an encrypted tunnel for all data, including the Modbus traffic, protecting it from eavesdropping.
How often should I update the firmware on my inverters and ESS?
You should check for firmware updates from the manufacturer regularly, at least quarterly, or subscribe to their security bulletins. Apply security patches as soon as they are released and tested for stability. This ensures that any newly discovered vulnerabilities are fixed before they can be exploited.



Leave a comment
All comments are moderated before being published.
This site is protected by hCaptcha and the hCaptcha Privacy Policy and Terms of Service apply.