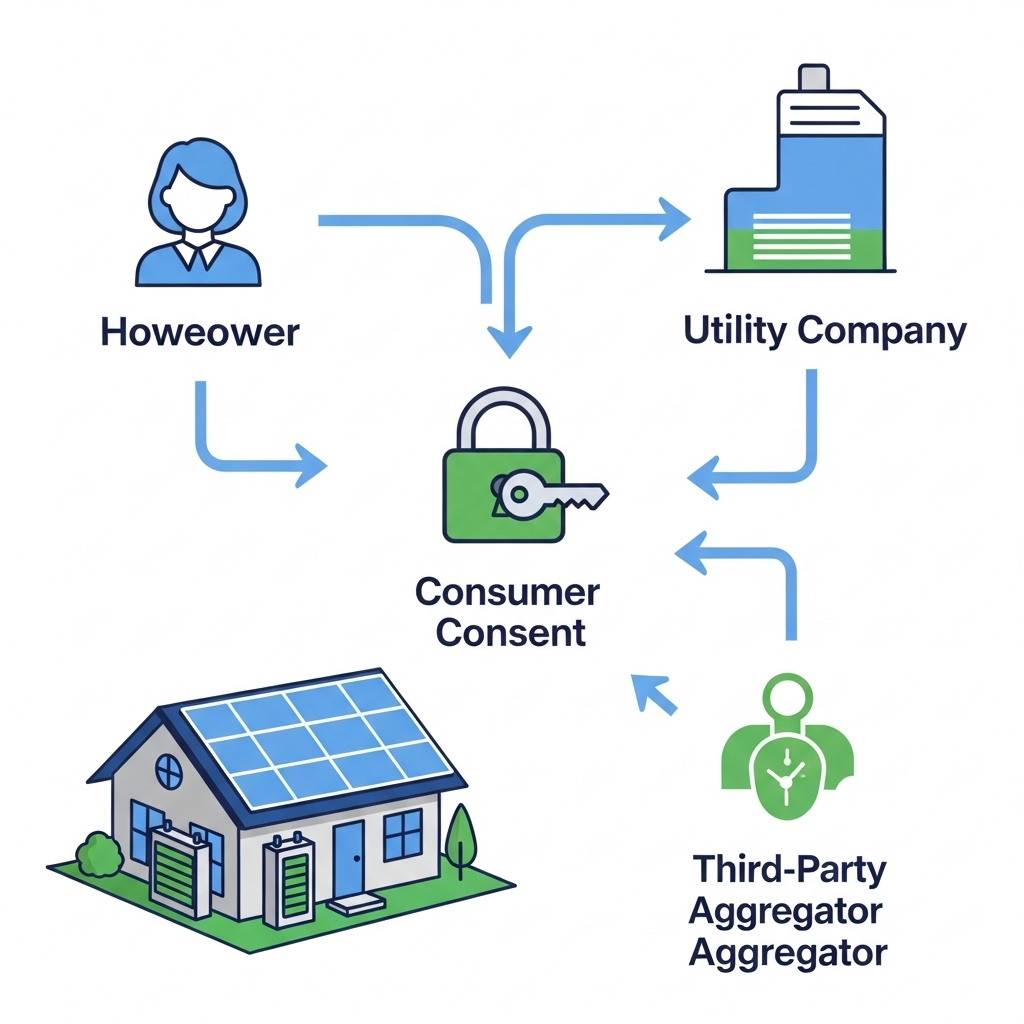
Distributed Energy Resources (DERs), such as rooftop solar panels and home battery storage, are reshaping our power grid. This evolution is driven by data. For the grid to operate efficiently and securely, it needs information from these devices. Yet, this raises critical questions about data access privacy and cybersecurity. A robust framework for DER data sharing, built on transparent user consent, is the key to unlocking this potential responsibly.
The Foundation of DER Data Sharing: Why Consent Matters
Before any data changes hands, establishing a clear and ethical foundation is paramount. This begins with understanding what data is involved and why consumer consent is not just a legal formality, but a cornerstone of trust.
What Data Are We Talking About?
DER systems generate a wealth of information. This includes energy production figures, consumption patterns, battery charge levels, and device performance metrics. For grid operators and service providers, this data is invaluable for balancing supply and demand, preventing outages, and creating new energy services. For consumers, it represents personal information about their daily lives and routines.
The Consumer's Right to Privacy
The data from a home's energy system can reveal a lot about personal habits. As a report on Grid Codes for Renewable Powered Systems notes, monitoring local consumption can lead to conclusions about user behavior. Protecting this information is crucial. Any data sharing framework must prioritize privacy protection through controlled access and carefully designed aggregation procedures. Building consumer trust through transparent consent management is non-negotiable for the success of a decentralized grid.
The Regulatory Landscape
Governments are actively developing rules for this new energy era. For instance, Germany's Law for the Digitalisation of the Energy Transition established a comprehensive framework covering metering requirements, data-sharing processes, and security protocols. As noted in an IEA report on power system transformation, these policies are vital for coordinating data collection and defining responsibilities between different grid stakeholders, ensuring a secure and organized transition.
Building a Robust Consent Management Framework
A successful consent strategy is not a simple checkbox. It is an ongoing dialogue with the user, empowering them with control and clarity over their personal information.
The Principles of Valid Consent
For consent to be valid, it must be freely given, specific, informed, and unambiguous. This means using clear, simple language instead of dense legal text. It also means no pre-ticked boxes or default opt-ins. The user must make a conscious and affirmative choice to share their data after being properly informed about how it will be used.
Granular Control: Empowering the User
Effective consent management provides users with granular control. They should be able to decide precisely what data they share, who they share it with, and for what purpose. For example, a user might consent to sharing aggregated performance data for grid stability but not real-time consumption data for marketing. This level of control fosters trust and encourages greater participation in DER programs.
Lifecycle Management: From Consent to Revocation
Consent is a dynamic process, not a one-time event. Users must have an easily accessible way to review their data sharing permissions, modify them, or revoke consent entirely at any time. A clear and straightforward process for managing the entire lifecycle of consent demonstrates a commitment to user privacy and control.
Technical Mechanisms for Secure Data Sharing
Strong policies must be supported by secure technology. The right technical architecture ensures that data is protected at every stage, from collection to transmission and analysis.
The Role of Data Hubs and Platforms
Many regions are establishing data platforms to manage the flow of energy information. Some European countries have implemented centralized data hubs that allow consumers to see their own data and authorize third-party access. According to the IEA, these platforms can help service providers develop new offerings for demand response and energy efficiency, provided there are clear privacy and data ownership guidelines.
Anonymization and Aggregation Techniques
Two powerful techniques for protecting privacy are anonymization and aggregation. Anonymization removes personally identifiable information from the data. Aggregation combines data from multiple users into a larger dataset, making it impossible to single out an individual's behavior. These methods allow grid operators to get the insights they need without compromising consumer privacy.
Access Control and Encryption
Strict access controls ensure that only authorized parties can view or use the data. This is often achieved through robust authentication and authorization protocols. Furthermore, all data should be protected with strong, end-to-end encryption, both when it is stored (at rest) and when it is being transmitted (in transit). This prevents unauthorized interception and is a fundamental component of cybersecurity for DER.
Practical Implementation and Best Practices
Applying these principles requires a focus on user experience and seamless integration. The goal is to make compliant data sharing a simple, transparent, and trustworthy process for the end-user.
Designing User-Centric Consent Interfaces
The interface where users grant consent should be a model of clarity. Use a layered information approach. Provide a simple, easy-to-read summary upfront, with options for the user to access more detailed information if they wish. Avoid jargon and focus on communicating the value and the risks in plain language.
Integrating Consent into the DER Onboarding Process
The best time to request consent is during the initial setup and onboarding of a new DER system. By making it a natural part of the installation process, you can educate the user from the start. This ensures they understand how their system contributes to the larger energy ecosystem and how their data plays a role.
Performance Metrics vs. Raw Data
Often, it is not necessary to share raw, high-frequency data. Sharing key performance indicators can provide sufficient information for many grid services while minimizing privacy risks. This approach aligns with the principle of data minimization—collecting only what is necessary. Understanding which metrics matter is key; for instance, the ultimate reference on solar storage performance outlines critical indicators like round-trip efficiency and depth of discharge that are useful for grid services without revealing personal habits.
Moving Forward with Trust and Transparency
Compliant DER data sharing is not a barrier to innovation. It is an enabler. By placing transparent consent, robust security, and user control at the center of our energy systems, we build the trust necessary for a decentralized grid to thrive. This approach ensures that the future of energy is not only cleaner and more resilient but also respectful of individual privacy.
Frequently Asked Questions
What is DER data sharing?
DER data sharing is the process of collecting and transmitting information from distributed energy resources, like solar panels and batteries, to utilities, grid operators, or third-party service providers. This data is used to improve grid stability, manage energy flow, and enable new services.
Why is consent management so important for DERs?
Consent management is critical because DER data can reveal sensitive information about a household's activities and lifestyle. A proper consent framework ensures users have control over their personal data, builds trust, and is often a legal requirement for data privacy.
Can I change my data sharing preferences after giving consent?
Yes. A compliant consent management system must allow users to easily review, modify, or completely revoke their consent at any time through a user-friendly interface.
What happens to my data if I revoke consent?
When you revoke consent, the authorized parties must stop collecting your data going forward. The specific policies regarding already-collected data may vary, but they should be clearly outlined in the privacy policy and terms of service.




Leave a comment
All comments are moderated before being published.
This site is protected by hCaptcha and the hCaptcha Privacy Policy and Terms of Service apply.