As solar energy systems become more interconnected, their digital security is increasingly important. Solar inverters, the brains of any photovoltaic system, are a critical component. They manage power flow, communicate with the grid, and report performance data. This connectivity, while beneficial, also creates potential vulnerabilities. The IEC 62443 standard offers a robust framework to address these security challenges, particularly for the firmware that controls every aspect of an inverter's operation.
Understanding IEC 62443: A Framework for Industrial Cybersecurity
The IEC 62443 series of standards is designed to secure Industrial Automation and Control Systems (IACS). While its roots are in traditional industrial settings like manufacturing plants, its principles are directly applicable to modern energy infrastructure, including distributed solar installations. It provides a systematic, risk-based approach to cybersecurity, moving beyond simple checklists to create a truly resilient defense.

Key Concepts: Zones, Conduits, and Security Levels
IEC 62443 organizes systems into logical parts to manage security effectively. Understanding these concepts is key to appreciating its approach:
- Zones: A zone is a grouping of physical or logical assets that share common security requirements. For instance, all inverters on a solar farm could be in one zone, while the remote monitoring platform could be in another.
- Conduits: These are the communication pathways that connect zones. A conduit could be a local network cable or the internet connection used for remote monitoring. Securing these conduits is vital to prevent unauthorized access between zones.
- Security Levels (SL): This concept defines how robust a system's security is. The levels range from SL 1 (protection against accidental misuse) to SL 4 (protection against sophisticated, nation-state-level attacks). The required SL for a solar inverter depends on a thorough risk assessment of its application.
| Security Level (SL) | Protection Against | Example Threat Actor |
|---|---|---|
| SL 1 | Casual or coincidental violation | Unskilled individual, accidental misuse |
| SL 2 | Intentional violation using simple means | 'Hacktivist' with generic tools |
| SL 3 | Intentional violation using sophisticated means | Skilled cyber attacker, organized crime |
| SL 4 | Intentional violation using sophisticated means with extensive resources | Nation-state agency |
Applying IEC 62443 to Solar Inverter Firmware
Inverter firmware is the operational software that dictates everything the device does. A malicious modification could have severe consequences, from system shutdowns to destabilizing the local power grid. IEC 62443 provides a clear roadmap for securing this critical software layer, especially during updates.
Why Inverter Firmware is a Prime Target
Compromising inverter firmware can allow an attacker to take control of the device. This could be used to disrupt power generation, feed false data to grid operators, or damage the hardware itself. As noted in a report by the International Energy Agency, the stability of the grid relies on the predictable behavior of connected assets like inverters. Remote access for monitoring and updates, while convenient, creates a potential attack vector that must be secured.
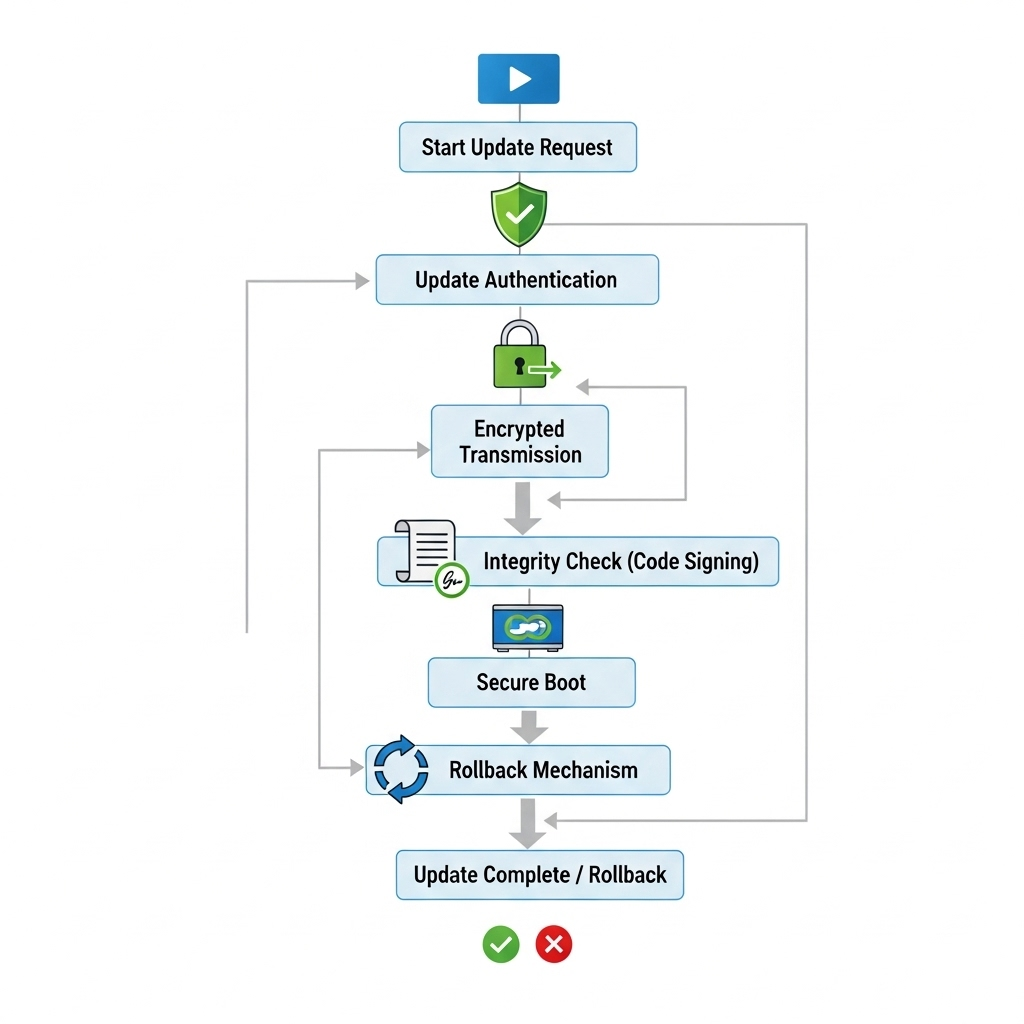
Securing the Firmware Update Process
The process of updating firmware is a moment of heightened vulnerability. IEC 62443 principles directly address this through several layers of defense:
- Authentication: The system must verify the identity of the person or system initiating the update. This prevents unauthorized users from pushing malicious code.
- Authorization: Once authenticated, the user must have the proper permissions to perform a firmware update. This is often managed through role-based access control.
- Integrity: The firmware file itself must be protected from tampering. This is achieved using cryptographic signatures. The inverter verifies the signature before installation to ensure the code is authentic and unaltered.
- Confidentiality: The firmware update package should be encrypted while in transit across a conduit (the internet), preventing eavesdroppers from capturing and analyzing it.
The Role of Remote Monitoring Channels
Remote monitoring portals are powerful tools, but they are also conduits that require strong security. According to the U.S. Department of Energy, securing these channels is paramount. One advanced method involves using data diodes, which physically restrict data to flow in only one direction. As described in a DOE-funded project, this technology can send telemetry data out for monitoring while physically blocking any incoming cyberattacks.
Practical Implications for System Owners and Installers
Adopting a security-first mindset is crucial for everyone involved in the solar industry. IEC 62443 provides a valuable guide for making informed decisions about technology and processes.
Selecting Secure Inverters
When choosing an inverter, ask the manufacturer about their security development lifecycle and their alignment with IEC 62443. Look for specific features that indicate a commitment to security, such as signed firmware updates, encrypted communications, and robust access controls. These features provide tangible protection for your energy asset.
Best Practices for Firmware Management
Technology alone is not enough. Secure processes are equally important. Always use strong, unique passwords for any system portals. When possible, segment your network to isolate inverters and other operational technology from general-purpose computers and devices. Maintain a strict policy for vetting and applying firmware updates from trusted sources only.
Performance and Security: A Balancing Act
Security measures should not come at the cost of system performance. A well-designed, secure inverter operates efficiently without compromising its defenses. In fact, strong security contributes to better long-term performance by preventing disruptions. As detailed in the ultimate reference for solar storage performance, system reliability is a function of both high-quality hardware and trustworthy software. Secure firmware ensures your system operates as intended, maximizing energy production and component lifespan.
A Stronger, More Resilient Grid
Ultimately, securing individual solar inverters contributes to the resilience of the entire energy grid. IEC 62443 provides the necessary framework for manufacturers, installers, and asset owners to work together towards a common goal. It encourages a proactive, defense-in-depth strategy where security is built into every layer of the system. By prioritizing solar inverter firmware security, you are not just protecting a single device; you are safeguarding your energy independence and contributing to a more stable and reliable energy future.
Frequently Asked Questions
Is IEC 62443 mandatory for solar inverters?
While not always a legal requirement, IEC 62443 is rapidly becoming a global benchmark for industrial cybersecurity. It is often a requirement for utility-scale projects and is considered a best practice across the industry. Choosing products developed with this standard in mind is a strong indicator of a manufacturer's commitment to security.
How does IEC 62443 differ from other standards like ISO 27001?
ISO 27001 focuses on the Information Technology (IT) world, providing a framework for an organization's overall Information Security Management System. IEC 62443, in contrast, is specifically tailored for the Operational Technology (OT) environment, addressing the unique security needs of industrial control systems like solar inverters.
Can a residential solar system owner benefit from IEC 62443 principles?
Yes. While a homeowner won't conduct a formal IEC 62443 audit, they benefit directly by choosing inverters from manufacturers who follow the standard. This ensures the product has foundational security features, such as secure remote updates and encrypted data transmission, which protect their investment, their data, and their home network.
What is a 'grid-forming' inverter and why is its security so important?
A grid-forming inverter can create its own stable power grid, a feature essential for microgrids and backup power. A U.S. Department of Energy project demonstrated their ability to restart a grid after a complete blackout. Because they have such a high level of control, their security is paramount. A compromise could have significant and immediate impacts on local grid stability.




Leave a comment
All comments are moderated before being published.
This site is protected by hCaptcha and the hCaptcha Privacy Policy and Terms of Service apply.